I was working with a start-up CISO, recently on “whats” and “hows” of CyberSecurity adoption. Full disclosure, the whole adoption canvas looked so scary with his lens. It became important for me to explain in steps the minimalist approach to adopt to help the company propel growth and at least exit the “death valley.” The discussions were very different from my talks with traditional Enterprise CISOs, and hence I believed this was worth a write up.
So let us remind ourselves why is Cybersecurity adoption so scary ? Not doing anything could be nice, at-least until unnoticed by the dark world. But doing something wrong could be catastrophic since there are more negative stakeholders, becoming punitive on you. There are attackers who want to exploit your business systems and extract dollars. Their so called “persistent” efforts lead to major global events – ransomware attacks, DDOS attacks, money siphoning, hacking etc. And I would not shy away from the fact that we also commit operational oversights which lead to global outage just like CrowdStrike 2024.
Now that we know we have to adopt at-least 5 complexity surfaces:
- Dealing with a plethora of technology providers, tools and software architectures making design, architecture and operations so difficult
- Dealing with controllers, regulators and compliance teams who puts a bunch of rules and policies inside those layers of tools and softwares
- Making it even worse complex hosting options on-prem, private cloud, COLO or SaaS, hyperscalers; and along with it comes a daunting separation of duties and obvious ball drops
- Having straightened all these starts the decision on implementing and running reliably – in-house or engaging an MSSP or a product vendor offering vertical and horizontal solutoions
- And finally making a compelling financial case in front of the CFO
My MSMV approach, or “minimal strategy for maximal value,” is crucial for such complex technology adoption.
Four aspects in consideration today, to handle the 5 complexities above:
- Understanding the “S-curve” of cyber adoption based on stage and type of business the firm is in.
- Understanding some of the “choice of tools, and providers”. Well there are lot many players, the grid is based on my experience and evaluation?
- How to get the signals where adoption course-correction is necessary ?
- Finally who do we entrust to build and run in a cost efficient, reliable, and scaled manner?
- Understanding the S-curve of Cyber adoption

At the start-up stage, your primary focus should be on basic security. This is crucial to run your business effectively. It also helps you exit the death valley. Depending on your business, you might need specialized security offerings. This applies if you are creating blockchain products or partnering for IT / OT device manufacturing. You may also need them as a quantum computing algorithm writer. They are necessary if you are a SAP intensive service provider. They are also essential for a consumer internet business needing advanced threat intelligence. Either way, your 0-3 years might appear more beefed up. These basic “run the business” security offerings help care for your core business.
There are also cross-functional and discretionary aspects of use based on the type of enterprise priorities and maturities. For example, you might choose to (a) having a dedicated security awareness and training wing, (b) having periodical BIC (Business impact analysist) and testing for BCP / DR strategies, (c) the storage, back-up and retention policies that are crucial for business continuity, (d) the file, folder, document management strategy and granting access to internal users, (e) data privacy needs, (f) Agentic AI run ops, (g) Security mesh architecture preference etc that might influence different level of security posture adoption and management.
2. Understanding some tools / providers to achieved a less diverse and more consolidate tool strategy so that it eases (a) operations, (b) manages complexity of change, (c) gives the buyer bargaining power, (d) helps achieve efficiencies in market.
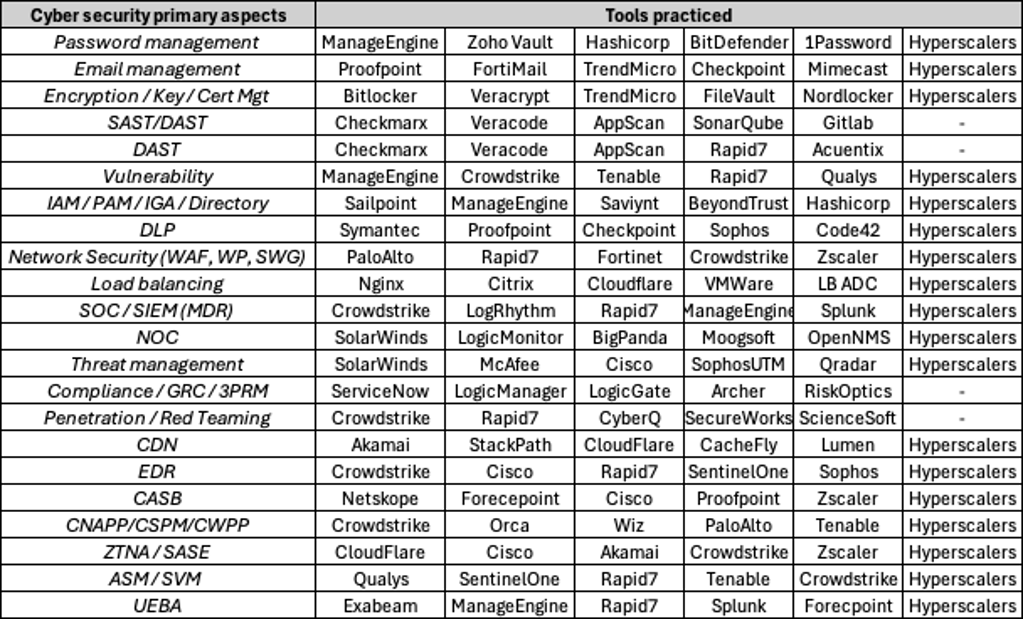
Some guardrails:
If there is a very focused need for a particular offering of cyber, as given in the adoption curve, then choosing one vendor is easy.
But if multiple solutions are needed, it is best to find one provider. This provider should offer the span of needs to yield ease of operations, talent management, and pricing competitiveness through bundling.
Further if you also need deployment or hosting solutions considering hyperscaler options is always beneficial
If you have a heavy on-prem, colo presence then building “home-grown” capabilities might make economic sense.
3. How to get the signals where adoption course-correction is necessary?
To shape up your cyber strategy you must have started with architecturally sufficient use cases to test your hypothesis works for maximal protection.
Your use case must navigate through the full mesh of technology layers starting from your internet to gateways to load balancers, firewalls, server instances, application, integration, database, authentication, cross data centre access and so on so forth. Each of these layers will interoperate with softwares, programming constructs, configured rules, tolerance parameters etc and you must have an “expected outcome” also called non-functional requirements, traceable at various levels of volume, timings, access points.
So when do you need adoption course-correction:
- If the outcomes breaches the levels of tolerance.
- If the based business process changes upon which the use case was defined.
- If the traffic and access patterns, distribution patterns of your products and services change.
- If an underlying technology modernization, or system interaction change happens.
- If there are additional actors or workflows injected in between.
- And assuming your have observability, telemetry driven AI / ML enabled operations which means you are listening to your events and alerts you know whether your base strategy is working or needs a change.
4. Finally how do we entrust to build and run in a cost efficient, reliable, and scaled manner?
In Cybersecurity implementation and operations, one of the major problems is the optionality of the primary partner. This is more significant than in any other technology offerings. It has huge regulatory and compliance implications. There are data privacy needs, and we know how policies and processes can build or destroy a moat. The reliability of multiple partners promising gold and platinum becomes a factor of dilemma. Additionally, there’s the challenge of building a decent mix of domain, function and technology prowess. Managing budgets granted by the CFO is crucial too to balance out CAPEX and OPEX decisions.
Selecting who ? In-house or MSSP / SI or Partner vendors?
That one vendor provides multiple options, leads to overlap of capabilities. It also results in redundancy of tools. Now there are MSSP and System Integrator who claim dexterity in implementing and running complex architectures. The enterprise now faces risks in managing too many vendors. There is also tool utilization dilution and complexity of operations. Additionally, pricing exploitation and risk and compliance are concerns. There is also a concern about future scalability.
If you as a CIO have a matured in-house IT, engage the Cyber partner vendor. Implement with the CISO. Make sure you understand dynamics of technology evolution, strategy and adoption, while you take operations inhouse.
If you have a clear relationship edge and pricing power with the vendor, proceed with the contract yourself. Ensure you have a strong procurement wing to assist in the negotiation. If you lack pricing power or a procurement wing, engage a VAR. They will negotiate and manage the contract on your behalf with your vendor.
If you are overwhelmed with the complexity of your systems, consider bringing in an SI / MSSP. This includes aspects like policies, process, domain expertise, and covering critical use cases during MVP. Deployment options and enterprise architecture may also be challenging. You might have to negotiate with multiple vendors and hosting providers. You can leverage their domain talent which acts as key input to Cyber protection assessment and transformation use case. Risk and compliance expertise is also key for success. Pricing and negotiaion power comes automatically with big SIs / MSSP managing multiple clients under one logo or tenancy. Talent scalability across the plethora of Cyber functions is challenging. Coverage and location needs of your business also is convenient to manage for global SI / MSSP players. Most importantly, they can help you demystify the world of AI, Gen-AI, Agentic-AI, and CoPilot. They also assist in implementing the minimalistic architecture for threat intelligence, Cyber operations management, BCP, DR, and more.
Summary
To conclude, my talk track to all CIO / CISOs is that implementing and adopting Cyber strategy is critical yet daunting. We must consider a multitude of factors around our minimal needs. These include the solution model, design patterns, technology and tools adoption, vendor selection, and operating principles. This approach will help our business grow safely and not limit its potential. Careful due-diligence and advisory is a must to create the befitting strategy. Bear in mind, it is an ongoing journey. It needs to be constantly curated with the changing business and IT ecosystem. Critical to survival is ensuring responsible governance, managed risk and compliance balanced out with cost efficiency and business agility.
Note: Each topic and line item above is worthy of debate and discussions, curated to your context. This is necessary to maximize the value of strategy. Also, I maintain no financial or investment positions in any or all the tools mentioned above. These are just point of view and might differ across specialists, analysts, and expert networks

Leave a comment